
Stuxnet could spread stealthily between computers running Windows—even those not connected to the Internet. If a worker stuck a USB thumb drive into an infected machine, Stuxnet could, well, worm its way onto it, then spread onto the next machine that read that USB drive. Because someone could unsuspectingly infect a machine this way, letting the worm proliferate over local area networks, experts feared that the malware had perhaps gone wild across the world.
In October 2012, U.S. defense secretary Leon Panetta warned that the United States was vulnerable to a “cyber Pearl Harbor” that could derail trains, poison water supplies, and cripple power grids. The next month, Chevron confirmed the speculation by becoming the first U.S. corporation to admit that Stuxnet had spread across its machines.
Although the authors of Stuxnet haven’t been officially identified, the size and sophistication of the worm have led experts to believe that it could have been created only with the sponsorship of a nation-state, and although no one’s owned up to it, leaks to the press from officials in the United States and Israel strongly suggest that those two countries did the deed. Since the discovery of Stuxnet, Schouwenberg and other computer-security engineers have been fighting off other weaponized viruses, such as Duqu, Flame, and Gauss, an onslaught that shows no signs of abating.
This marks a turning point in geopolitical conflicts, when the apocalyptic scenarios once only imagined in movies like Live Free or Die Hard have finally become plausible. “Fiction suddenly became reality,” Schouwenberg says. But the hero fighting against this isn’t Bruce Willis; he’s a scruffy 27-year-old with a ponytail. Schouwenberg tells me, “We are here to save the world.” The question is: Does the Kaspersky Lab have what it takes?
Viruses weren’t always this malicious. In the 1990s, when Schouwenberg was just a geeky teen in the Netherlands, malware was typically the work of pranksters and hackers, people looking to crash your machine or scrawl graffiti on your AOL home page.
Symantec believes it has been used for what could be state-sponsored attacks to infiltrate 36 computers across at least seven organizations around the world - Its targets include several individuals in Russia, a Chinese airline, an unnamed organization in Sweden and an embassy in Belgium.








 Reply With Quote
Reply With Quote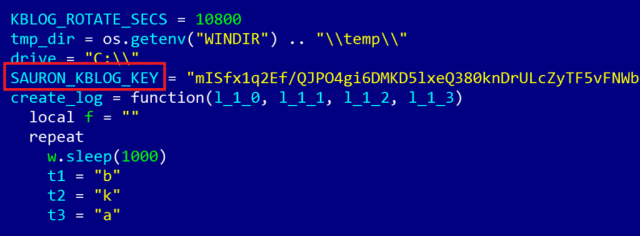












Bookmarks