Promo for new German-Spanish film on the legal fight surrounding Assange (english subtitles) -
Hacking Justice
Awesome team and they don't get paid, a clip from the film of the legal team at work can be viewed here.Published on May 19, 2017
Click here to register
http://www.docsonline.tv/world-premie...
When you're more than a journalist, you need more than a lawyer !
May 19th 2017, Swedish Prosecutor Marianne Ny drops charges against Julian Assange.
A victory for international legal team lead by Judge Garzon, over a four year endeavour documented by "Hacking Justice", unique film available on the topic with non-infringed image rights from all appearing parties.
Baltasar Garzon, 58, is an analogue man, barely speaks english, is bad with computers. But he plays a major global role within the digital world. He took upon coordinating the international legal teams preparing the upcoming defense of WikiLeaks founder Julian Assange. Garzon is one of the world’s leading authorities upholding the principle of Universal Jurisdiction, defending in this case freedom of press but also fundamental human rights. With a unique access, the film witnesses the struggle for the control of information, the growing influence of intelligence services, the lack of transparency, the role of the mass media and the difficult balance of individual rights and state security.
* * *
Podcast: WBAI Free Assange #5 -- interview with police corruption whistleblowers, Frank Serpico -
http://nuarchive.wbai.org/mp3/wbai_1...andyCrelof.mp3 …
wbai.org
- Home
- Forum
- Chat
- Donate
- What's New?
-
Site Links

-
Avalon Library

-
External Sites

- Solari Report | Catherine Austin Fitts
- The Wall Will Fall | Vanessa Beeley
- Unsafe Space | Keri Smith
- Giza Death Star | Joseph P. Farrell
- The Last American Vagabond
- Caitlin Johnstone
- John Pilger
- Voltaire Network
- Suspicious Observers
- Peak Prosperity | Chris Martenson
- Dark Journalist
- The Black Vault
- Global Research | Michael Chossudovsky
- Corbett Report
- Infowars
- Natural News
- Ice Age Farmer
- Dr. Joseph Mercola
- Childrens Health Defense
- Geoengineering Watch | Dane Wigington
- Truthstream Media
- Unlimited Hangout | Whitney Webb
- Wikileaks index
- Vaccine Impact
- Eva Bartlett (In Gaza blog)
- Scott Ritter
- Redacted (Natalie & Clayton Morris)
- Judging Freedom (Andrew Napolitano)
- Alexander Mercouris
- The Duran
- Simplicius The Thinker





 Reply With Quote
Reply With Quote

 Miroslav Stampar @stamparm
Miroslav Stampar @stamparm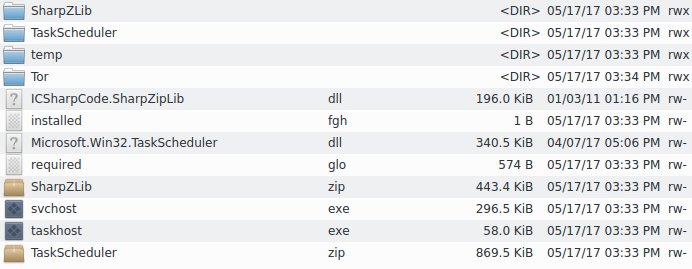








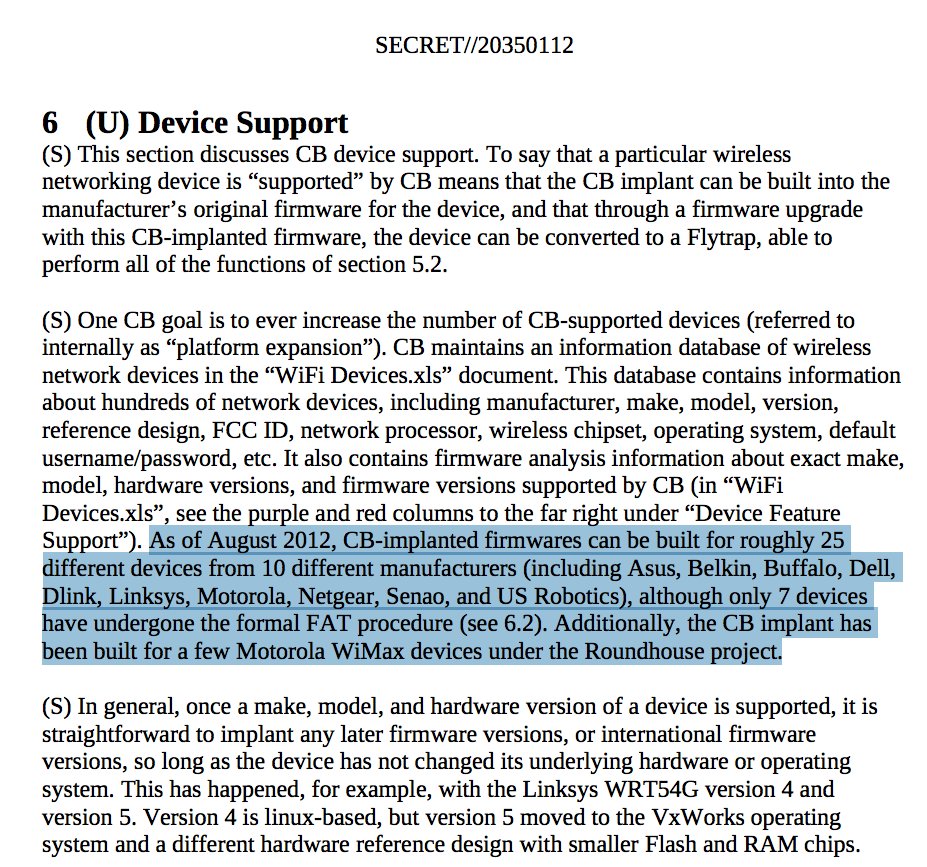


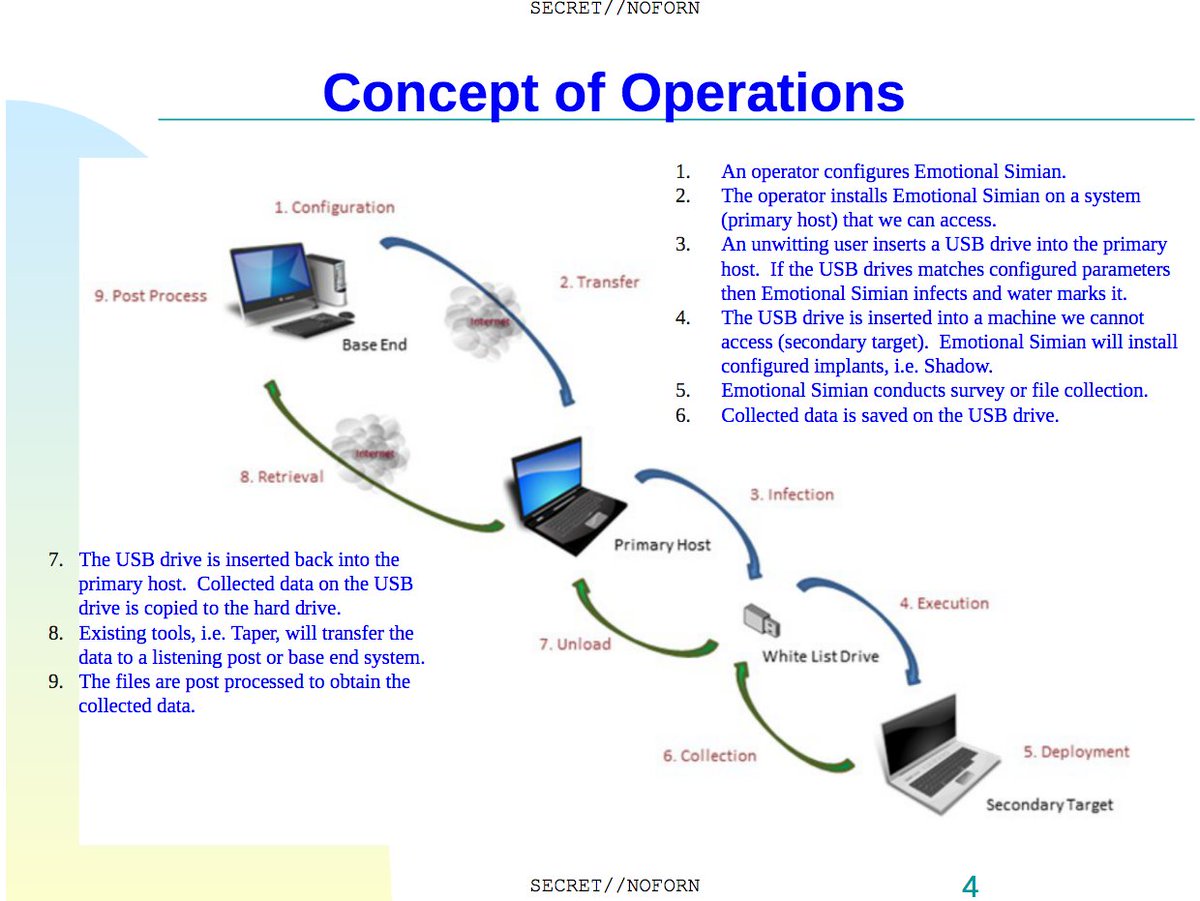
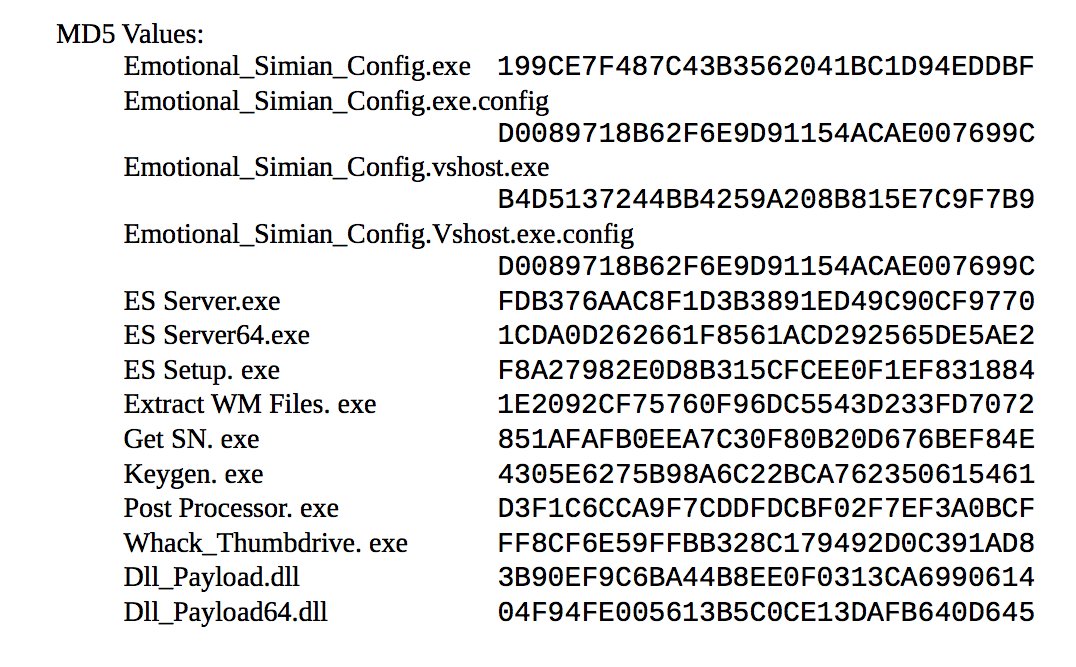

 WikiLeaksVerified account @wikileaks
WikiLeaksVerified account @wikileaks
 Julian Assange @JulianAssange
Julian Assange @JulianAssange









Bookmarks