
WikiLeaks’ recent release, collectively dubbed “Vault 7”, made public thousands of documents and files that the organization claimed were sourced from a high-security network within the CIA – or at least what was supposed to be one.
According to WikiLeaks, this archive of data was circulating “in an unauthorized manner” among former US government hackers and contractors, including one who provided the Vault 7 information to WikiLeaks. The documents themselves, if genuine, reveal several alarming realities about the proliferation of high-quality malware, as well as the privacy risks presented by the hacking of connected devices that the average person uses every day.
While the revelations may be unsettling, they also shine valuable light on pertinent cybersecurity challenges faced by organizations today, and the nature of the security measures required to proactively address these concerns. Here are three particularly critical cybersecurity issues that the WikiLeaks release brings into stark focus:
1) Insider threats remain a dangerous risk area that perimeter security measures cannot address
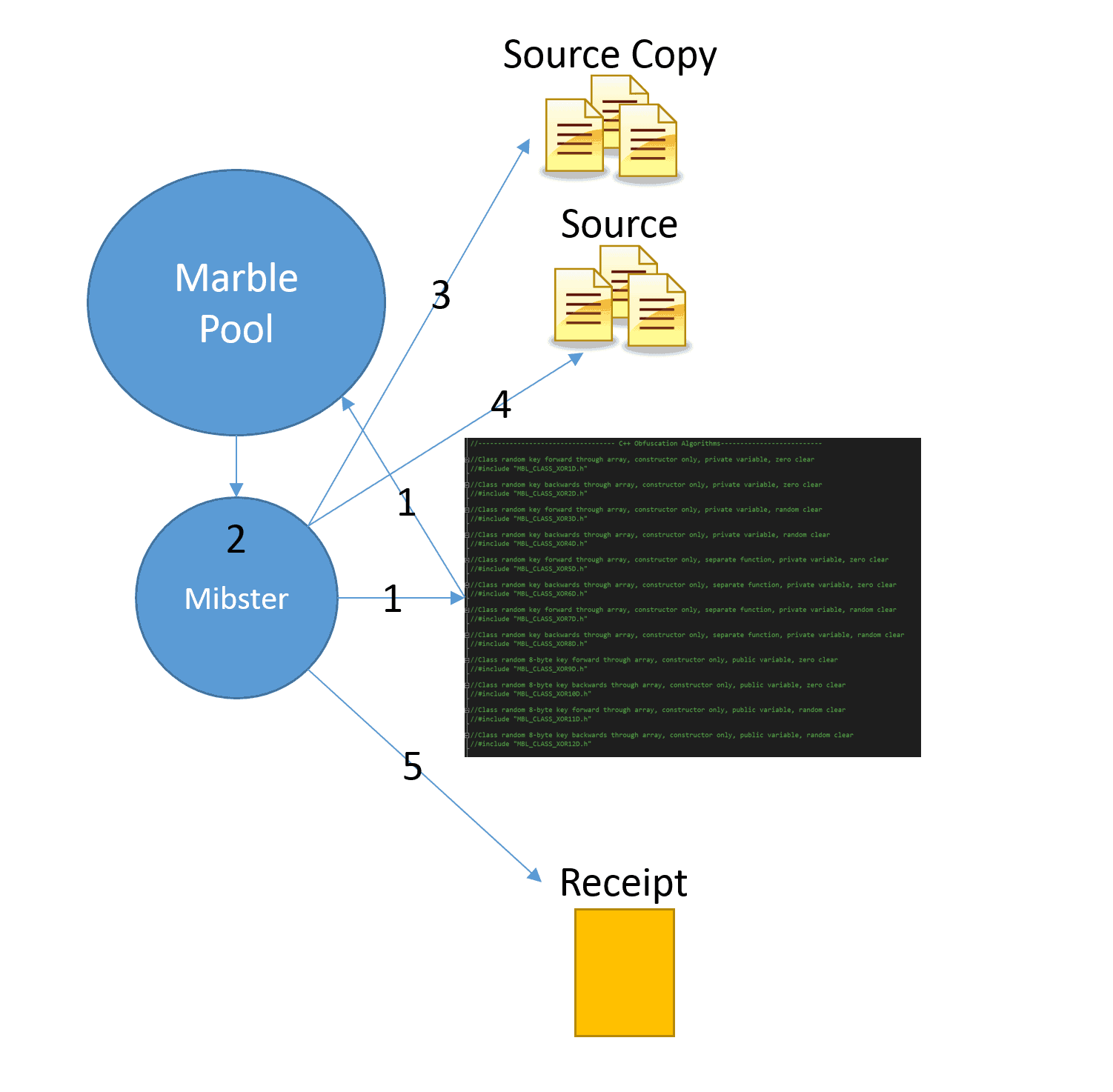
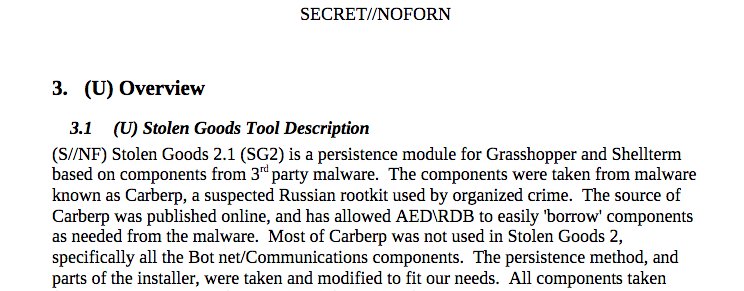
Whether you believe the WikiLeaks release is a bold stand for government transparency that should be celebrated, or a dangerous exposure of critical state secrets, this story actually includes two incidents of sensitive data revealed by insiders with access. The Vault 7 leak stipulates that the CIA created and then lost control of powerful malware and other tools for circumventing security measures on most popular computers and devices.
If accurate, these tools may now be in the hands of hackers and other entities with bad intentions. Just as the Vault 7 information was given to WikiLeaks by an insider, the CIA’s hacking arsenal was supposedly exposed in the same manner.
Enterprises
spend a collective $12 billion dollars each year on cybersecurity solutions designed to protect sensitive data by safeguarding against perimeter breaches. However, these solutions are powerless against the threat of insiders with valid access and credentials leaking data. Research from IBM found that
60% of all cybersecurity attacks involve insiders, with three-quarters of those insiders acting maliciously, and the remainder inadvertently – but no less dangerously – supporting the attacks. A separate study by Accenture discovered that
69% reported experiencing such an attack within the past year.
Faced with insider threats, organizations should look to IT strategies capable of proactively identifying sensitive information on their networks, and safeguarding it across all endpoints and data storage locations. Such solutions can protect sensitive data from being disseminated by insiders with access, whether on purpose or by mistake.
2) Malware and other hacking tools are more prevalent and capable than ever
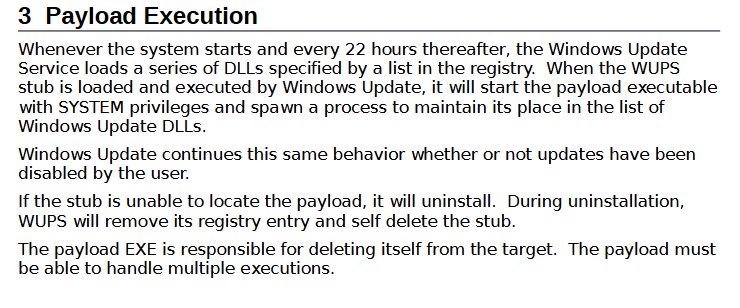
A major implication of the Vault 7 release is that individual hackers may now be able to conduct cyber-attacks with a sophistication previously only seen in state-sponsored actions. While unique malware often plays a role in major cyber-attacks, the quality and dangers presented by the available tools present a heightened new level of risk.
In response, businesses should continue to deploy the most robust perimeter security they can muster, while preparing for the eventuality that highly-capable attacks will indeed penetrate this first line of defense. Anticipating this, perimeter security should be teamed with endpoint security able to detect, mitigate, and recover from any risk posed by these threats.
3) “Edgepoints” are a new frontier rife with security vulnerabilities
Privacy is a function of cybersecurity just as much as safeguarding information is, and a listening device or compromised camera can expose an organization’s sensitive data just as surely as malware can. Among the most frightening revelations in the Vault 7 leak is the thought that all the connected devices in our lives can be hacked and repurposed for surveillance.
The Internet of Things is growing rapidly, with manufacturers producing myriad connected devices with little regard for security – and sometimes none whatsoever. However, these vulnerable “edgepoints” are just as critical to organizational security as any endpoint device. Both the IoT industry and internal security measures must evolve to treat them as such.
The cybersecurity landscape suggested by WikiLeaks may be one where an organization’s defenses no longer have an effective perimeter, but it doesn’t have to be one with no secrets or privacy. Given our hyper-connected world and the fearsome tools now at a would-be attacker’s disposal, breaches will occur.
However, with the right strategies and solutions in place to safeguard sensitive data at the device level, organizations can ensure that that’s as far as hackers get.
23 March, 2017
Julian Assange answered questions on WikiLeaks latest release in ‘Vault 7,’ named ‘Dark Matter,' as well as the CIA’s ever-changing role and the impact this has on world affairs.










 Reply With Quote
Reply With Quote






 WikiLeaksVerified account @wikileaks
WikiLeaksVerified account @wikileaks
 Christine Maguire @_ChrisMaguire
Christine Maguire @_ChrisMaguire







Bookmarks