
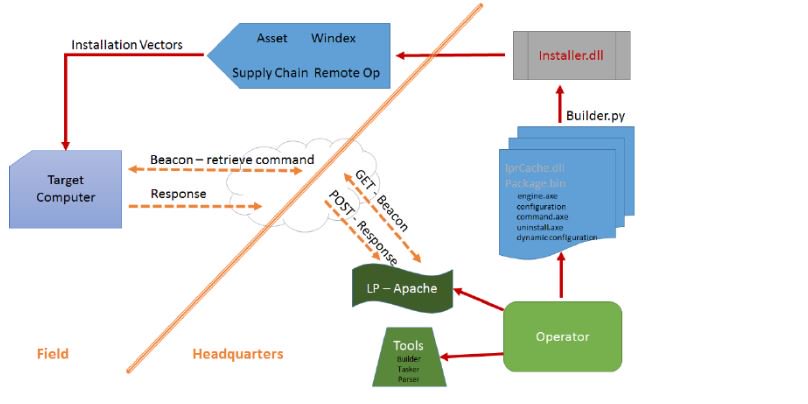
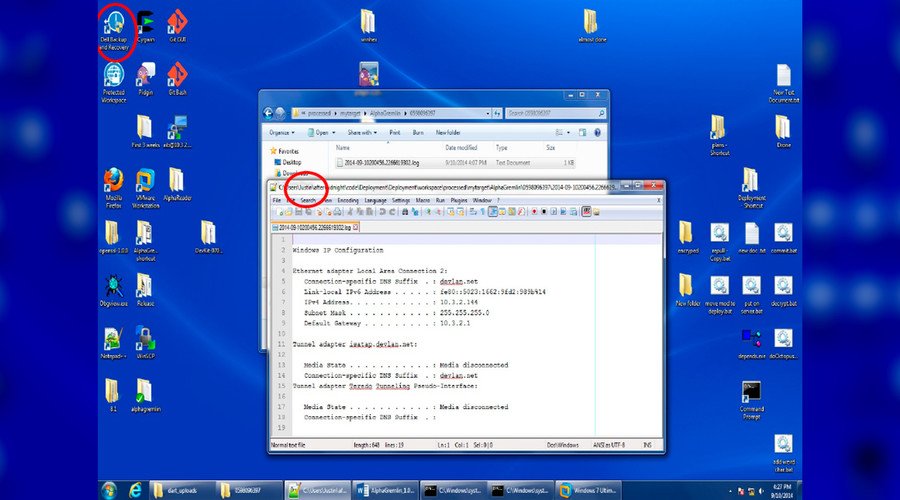
CIA Director Mike Pompeo recently called WikiLeaks a “hostile intelligence service.” Attorney General Jeff Sessions stated that Julian Assange’s arrest is a “priority” of the Trump administration. In response, numerous individuals — with differing perspectives on WikiLeaks — warn of a growing threat to press freedom.
Today at the Justice Department 2 former government officials addressed U.S. government policy toward WikiLeaks and whistleblowers:
* Ann Wright is a retired U.S. Army Reserve colonel, and a 29-year veteran of the Army and Army Reserves. As a U.S. diplomat, Wright served in Nicaragua, Grenada, Somalia, Uzbekistan, Krygyzstan, Sierra Leone, Micronesia and Mongolia and helped re-open the U.S. embassy in Afghanistan in 2001. In March of 2003, she resigned in protest over the invasion of Iraq. She is co-author of Dissent: Voices of Conscience.
* Ray McGovern, a former Army officer and CIA analyst who prepared the President’s Daily Brief (under the Nixon, Ford, and Reagan administrations), is co-founder of Sam Adams Associates for Integrity (see: samadamsaward.ch), which gave Julian Assange its annual award in 2010. Sam Adams Associates strongly opposes any attempt to deny Julian Assange the protections that are his as a journalist.
Contact at ExposeFacts (a project of the Institute for Public Accuracy):
Sam Husseini, (202) 347-0020, sam [at] accuracy dot org.









 Reply With Quote
Reply With Quote


 WikiLeaksVerified account @wikileaks
WikiLeaksVerified account @wikileaks















 Colm McGlinchey @ColmMcGlinchey
Colm McGlinchey @ColmMcGlinchey
 RTVerified account @RT_com
RTVerified account @RT_com

Bookmarks